Safer Mobile
Posted by MelissaLoudon on Oct 14, 2011
Mobile Tools for Backups, Data Deletion and Remote Wipe data sheet 1870 Views
Abstract:
Anyone who has had a phone stolen knows the frustration of trying to rebuild your contact list, not to mention data on the phone that is unrecoverable. Worse, the data stored on your phone can be dangerous in the wrong hands. In addition to being able to impersonate you to your mobile contacts, consider the risk of an attacker who has access to some of all of the following:
- Your saved contacts - names, phone numbers, perhaps also email addresses and physical addresses
- Call logs - calls made and received
- Stored text messages
- A calendar with your appointments, or a task list
- Your mobile email
- Your web browser with stored passwords
- Photos, video and sound recordings stored on the phone and memory card
- Data stored by applications - notes, social networking contacts and posts
Three kinds of tools can lessen the pain of losing your mobile data, and limit your risk should your phone be lost or stolen.
- Backup and restore tools allow you to save a backup of contacts and other data stored on your phone
- Data deletion tools can be used to ‘clean’ a phone completely before disposing of it, giving it away or travelling to a location where you are worried it could be stolen or confiscated
- Remote wipe tools are set up so that if your phone is lost or stolen, you are able to clean it remotely, deleting sensitive data. Many remote wipe tools also allow you to track the phone provided it has not been turned off.
Anyone who has had a phone stolen knows the frustration of trying to rebuild your contacts list, not to mention data on the phone that is unrecoverable. Worse, the data stored on your phone can be dangerous in the wrong hands. In addition to being able to impersonate you to your mobile contacts, consider the risk of an attacker who has access to some of all of the following:
- Your saved contacts - names, phone numbers, perhaps also email addresses and physical addresses
- Call logs - calls made and received
- Stored text messages
- A calendar with your appointments, or a task list
- Your mobile email
- Your web browser with stored passwords
- Photos, video and sound recordings stored on the phone and memory card
- Data stored by applications - notes, social networking contacts and posts
Three kinds of tools can lessen the pain of losing your mobile data, and limit your risk should your phone be lost or stolen.
Posted by MelissaLoudon on Oct 14, 2011
Securing your Mobile Email data sheet 2118 Views
Abstract:
Email wasn’t designed with security in mind. Unless you take steps to protect your communication, emails are sent in plain text - and so are your email account username and password.
At the same time, if you and your recipient are taking the appropriate security precautions, mobile email can be a secure and reliable alternative to other forms of mobile communication. If you have data service for your mobile, encrypted email can replace text messaging, and if you aren’t able to access a website securely to upload content - photos or videos for example - getting it to a trusted contact as an email attachment can be a safer alternative.
Email wasn’t designed with security in mind. Unless you take steps to protect your communication, emails are sent in plain text - and so are your email account username and password.
At the same time, if you and your recipient are taking the appropriate security precautions, mobile email can be a secure and reliable alternative to other forms of mobile communication. If you have data service for your mobile, encrypted email can replace text messaging, and if you aren’t able to access a website securely to upload content - photos or videos for example - getting it to a trusted contact as an email attachment can be a safer alternative.
This article suggests the following tactics for improving the security of your mobile email:
Email security basics
Even if you’re not using encrypted email, you can take some basic precautions to improve your email security. For example
Posted by ccarlon on Oct 13, 2011
Blacknoise: Low-fi Lightweight Steganography in Service of Free Speech data sheet 1064 Views
Abstract:
Censorship of communications is a widespread, current practice in various countries with repressive governments in order to prevent or restrict speech; political speech in particular. In many cases state-run telecommunications agencies including those providing internet and phone service, actively filter content or disconnect users in defense of incumbents in the face of widespread criticism by citizens.
In this paper I present Blacknoise, a system which uses commodity low-cost mobile telephones equipped with cameras, and takes advantage of their lowfidelity, noisy sensors in order to enable embedding of arbitrary text payloads into the images they produce. These images can then be disseminated via MMS, Bluetooth, or posting on the Internet, without requiring a separate digital camera or computer to perform processing.
Posted by MelissaLoudon on Sep 22, 2011
Particularly for smartphones, there are many apps that promise improved privacy and security for your mobile communications. Like all apps, some are very good, but other are poorly written or overpriced, and may even be malicious. This article will help you evaluate whether you should trust their promises.
Before You Start
Security apps are most useful as part of a coherent security policy covering all your mobile communications. The Mobile Risk Assessment Primer will help you complete an inventory of mobile communications risks, and decide which are most important and most feasible to mitigate.
Once you’ve completed a risk assessment, it’s important to search broadly for security apps. MobileActive is in the process of reviewing many of these from our current list of security apps, but the mobile security landscape changes quickly. Ask friends and colleagues, read about your specific security need online, and search your device’s app marketplace. Once you’ve identified as many options as possible, it’s time to start evaluating your security apps.
Will It Work on Your Phone?
As with computer software, some mobile apps are built to work on one platform - Android, iPhone, Blackberry, Symbian, Java - and may not work on others. There may be other requirements too, such as particular phone models. Make sure the apps you have chosen are all going to work on your device.
Also consider how you will actually get the app - can it be downloaded from a web link that you open on your phone, or can you get it from an app marketplace? Some apps can also be downloaded to a PC and transferred via bluetooth or a data cable. This step sounds obvious, but it can be tricky when you don’t have stable Internet access on your phone or aren’t used to the app install process.
Posted by SaferMobile on Aug 09, 2011
Safer Facebook data sheet 6165 Views
Abstract:
Facebook has more than 500 million users, half of which access the site through their mobile phone. Being able to communicate your message to an audience this large is exceptionally valuable. At the same time, your activities on the site generate very detailed information about you and your networks. If you are concerned about surveillance, this information can put you at risk. This how-to explains what those risks are and how to use Facebook on your mobile device more securely.
Facebook has more 500 million users, half of which access the site through their mobile phones. Being able to communicate your message to an audience this large is exceptionally valuable. At the same time your activities on the site generate very detailed information about you and your networks. If you are concerned about surveillance, this information can put you at risk.
Assess Your Facebook Mobile Risks
Like Twitter, Facebook is a way to get your messages to a potentially large audience. It is not a secure method of communication for sensitive information.
This article offers advice about how to mitigate risks when using Facebook as a dissemination and organizing tool. In particular, we consider the following risks:
- The risk that your public activities on Facebook reveal compromising information about you or your networks - for example, revealing the identity of supporters or identifying people who were present at a particular event.
- The risk of your private information being revealed to a third party without your consent.
- The risk that your account details (username and password) are discovered, and that someone may impersonate you.
- The risk of your account being deleted or suspended.
- The risk that Facebook is blocked or becomes inaccessible.
in general, you should only use Facebook to share information that you consider public. Public information can be freely distributed by you, your organization, and your supporters, without any risk to individuals or organizational operations. In communicating public information, you can send and receive this information without taking any precautions.
Posted by MelissaLoudon on Jul 11, 2011
HTTP, the Hypertext Transfer Protocol, is the data communication protocol you use when you broswe the web - as you probably know if you've noticed that website addresses usually begin with http://. HTTPS is the secure version of HTTP, which you might have seen being used for sensitive transactions like online banking and online shopping. When you are using the secure part of a site, the web address will begin with https://.
When using your mobile phone for sensitive communications, it is important to ensure that your online activities - whether researching or reading about an issue, sending an email, writing a blog post or uploading photos - are done over a secure connection. There are three elements of secure web browsing:
Posted by MelissaLoudon on Jun 30, 2011
Smartphones (iPhone, Android, Blackberry, Windows Mobile, Symbian) and many feature phones allow you to download and install mobile applications (“apps”). Apps do many useful things. However, some apps (and other types of software, such as your mobile operating system) can also present security risks. These include:
Apps and other software may have access to information stored on or generated by your phone.
Apps and other software may have the ability to transmit this information using your phone’s Internet connection.
Malicious apps or other mobile software installed on your mobile device can expose you to the following risks:
Your conversations may be listened to or recorded without your knowledge.
Your text messages, emails and web traffic may be monitored and logged.
Data stored on your phone (contacts, calendar entries, photos and video) may be accessed or copied.
Passwords stored or entered on your phone may be stolen and used to access your online accounts.
Your locationmaybetracked, even when your phone is switched off.
With smartphones gaining market share, malicious apps are beginning to pose a serious threat. In an article titled “Your Apps Are Watching You”, the Wall Street Journal tested popular iPhone and Android apps, and found that of 101 apps tested, 56 transmitted a unique identifier for the phone without informing the user or asking for consent. 47 apps also transmitted the phone’s location, while 5 sent age, gender or other personal details to various companies. The App Genome Project reports that 28% of all apps in the Android Market and 34% of all free apps in the Apple App Store have the capability to access location, while 7.5% of Android Market apps and 11% of Apple App Store apps have the capability to access users’ contacts.
It can be very difficult to tell which apps are safe and which are not. App behaviours that might not bother most users, such as transmitting the phone’s location to an advertising server, can be unacceptable to people with higher privacy and security requirements.
This article offers suggestions on how to assess risks to security and privacy posed by apps.
Posted by VivianOnano on Jun 29, 2011
Mobile Application Security data sheet 1834 Views
Author:
Dwivedi, Himanshu, Chris Clark, David Thiel.
Abstract:
A discussion on mobile application security must address the current issues facing mobile devices and the best way to mitigate them. This chapter aims to provide content on the following subjects:
- Top issues facing mobile devices
- Tips for secure mobile application development
The issues covered in this chapter are not exhaustive and appear in no particular order; however, they can be used to begin the conversation on mobile application security in your organization.
Posted by SaferMobile on Apr 25, 2011
NOTE: This article was updated with an addendum and additional data.
Inspired by Michael Benedict's original blog post on monitoring SMS delivery reliability in Tanzania and recent reports of SMS keyword blocking in Uganda, MobileActive.org set out to replicate Michael's work - and add to it. SMS is such a crucial part of many mobile projects and just day-to-day life across the developing world, yet there’s a lack of public knowledge of mobile network operator interdependency, latency, and reliability (how mobile network operators work together to transmit SMS, the lag time between sending and receiving a message, and the guarantee that a message will reach its recipient).
Michael's post got us thinking: Can this type of experiment be replicated without extra hardware required (GPRS modems, etc.)? After a few quick brainstorming sessions at the OpenMobile Lab in New York, we created an alpha version of a mobile application that recreates a number of latency tests. It’s far from perfect - and there is still plenty of work to be done - but we’re confident that this project will lead us to extremely valuable data about the transparency and reliability of SMS on mobile networks.
SMSTester - The App
SMSTester is a simple Android app that allows a user create a set of keywords to be sent as SMS messages. This allows the user to explore differences in latency for any type of message - from basic, everyday text like ‘milk’ or ‘newspaper’ to politically inflammatory text such as ‘revolution.’ We then set up a logging mechanism to timestamp and record each SMS as it is sent (from the sender side) or received (on the receipt side). By comparing the sent and received timestamps, we’re very easily able to calculate message latency from one SIM to another.
Initial Deployment
We deployed SMSTester in a test in Egypt a few weeks ago. As this was the initial trial for a fully untested application, we were careful. While we did run our tests across a number of local mobile operator networks, we kept the test volume small enough to keep us under the radar (for now!). Our test methodology included:
- Testing across all three major mobile operator networks in Egypt: Etisalat, Mobinil, and Vodafone
- Consistent keyword test bed containing both ‘safe’ and ‘political’ terms, where ‘safe’ refers to everyday vocabulary and ‘political’ refers to politically sensitive words
- Language coverage across both English and Arabic
- Roughly 270 messages successfully sent, received and analyzed
What We Looked For And Why
The main focus of our analysis was SMS delivery latency, delay, or more generally, delivery failures. There are plenty of anecdotal stories of seemingly random delays lasting multiple hours or even days in many countries where we work. While network congestion and growing infrastructure are often to blame for SMS unreliability, there are also legitimate concern that delays may be an indication of deliberate message filtering and monitoring. What has emerged is an environment in which activists and human rights defenders are unable to clearly understand what networks - and what behavior - is safe or hazardous for themselves or their contacts. The end goal of this research, put simply, is to change this paradigm. Rumors of keyword filtering are not helpful; what is helpful is any evidence of surveillance.
This small experiment is just a start, of course. Our hypothesis is that keyword filtering and other malicious behavior on the part of mobile network operators may manifest in the form of increased message latency or overt message blockage. If we could detect any sign of a correlation between message content and delivery with just some initial testing in-country, this would be a great first step towards our overall goal. However it’s very important to note that while message latency or failure may be indicative of bad behavior on the part of the carries, it could be due to any number of contributing factors and is by no means an implication of foul play. For now we’re merely hypothesizing.
Results
Despite the minor bugs discovered, we gathered very valuable information about message latency in Egypt during this trial. The most valuable data was on the Etisalat network (also known as the Emirates Telecommunications Corporation), based in the UAE. The majority of the data we recovered from this trial was between an Etisalat SIM and other Egyptian networks. (Note: This was the result of inadvertent data loss for other test scenarios and we did not specifically target Etisalat).
Main Conclusions
Big Caveat (READ THIS!): Given the small sample size of this test, it should be noted that none of these conclusions are definitive. In fact, the very nature of such a small sample size warrants much further investigation.
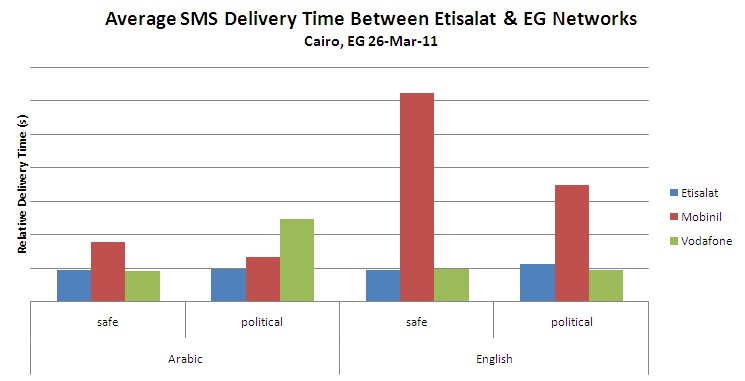
(1) Delivery between Etisalat & Mobinil networks warrants further investigation. As shown below, the delivery time for English language text messages from Etisalat to Mobinil is significantly greater than delivery time to any other network, for both English and Arabic texts. This may be due to any number of network delays, and it may also be indicative of English language filtering by one or both of the mobile network operators.
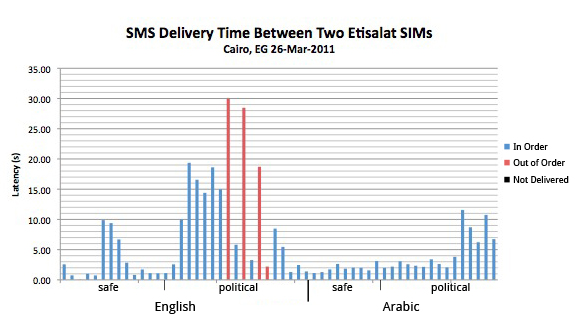
(2) Delivery time of politically sensitive English messages on Etisalat warrants further investigation. The chart below shows that politically sensitive English messages sent across the Etisalat network were delivered with significantly more latency than others, with the possible exception of politically sensitive Arabic messages. In addition, each of the three messages that were delivered out of order fell into this category. Similar to the above conclusion, this may be indicative of specific filtering on behalf of Etisalat.
| SMSTester - Monitoring SMS Delivery (and Keyword Filtering, Possibly) data sheet 6574 Views |
| Countries: |
Egypt
|